Learn More
B.Sc.IT programme will enable students to understand the basics of Cloud Technology and Information Security. As an evolving industry, this field will attract many career prospects and in order to fulfil industry demand Assam down town University encourages interested applicants to consider and enrol for this programme for a better career opportunity.
Year wise Course Details
Courses for this semester
The course ‘Logic and Mathematical Reasoning’ enables students to student to apply and logical thinking skills, an understanding of numbers, to various real-world applications. They will improve their reasoning skills as required by them in fulfilling their individual and organizational goals. The course exposes the students to ‘logical tools’ and ‘quantitative reasoning methods’ and enables them to apply these logical strategies in business decision-making.
The Storage Fundamentals course provides students with a broad survey of the current state of network storage. By focusing on concepts, terms, and technologies and avoiding product-specific features, this course provides foundation knowledge that applies to the further study of storage products.
Introduction to Operating Systems is a graduate-level introductory course in operating systems. This course teaches the basic operating system abstractions, mechanisms, and their implementations. The core of the course contains concurrent programming (threads and synchronization), inter-process communication, and an introduction to distributed operating systems. The course is split into four sections: (1) Introduction, (2) Process and Thread Management, (3) Resource Management and Communication, and (4) Distributed Systems.
C++ is a programming language with a special focus on the concepts of OOPs and their implementation. It has object-oriented features, which allow the programmer to create objects within the code. This makes programming easier, more efficient, and some would even say more fun. The Star C++ Programming certification course provides in-depth knowledge about C++. The course helps acquire a fundamental understanding of the OOPs concepts, input/output data management, arrays in C++, functions, classes, objects, pointers, and much more. The course has been designed with a uniform structured series of modules enumerating various pertinent concepts.
This Data Structures in C course covers the following topics with C language implementation: Algorithm Analysis, Big O notation, Time complexity, Singly linked list, Reversing a linked list, Doubly linked list, Circular linked list, Linked list concatenation, Sorted linked list.
This course will introduce you to modern operating systems. We will focus on UNIX-based operating systems, though we will also learn about alternative operating systems, including Windows. The course will begin with an overview of the structure of modern operating systems. Throughout the subsequent units, we will discuss the history of modern computers, analyze in detail each of the major components of an operating system (from processes to threads), and explore more advanced topics in the field, including memory management and file input/output. The class will conclude with a discussion of various system-related security issues.
This course will help develop applications for a range of problems using object-oriented programming techniques.
The course aims to equip students with a comprehensive understanding of data structures and algorithms. Through this course, students will learn about different data representation techniques that are commonly used in real-world scenarios. They will also gain practical experience in implementing both linear and non-linear data structures. Additionally, the course will provide students with the skills needed to analyze algorithms based on their time and space complexity. With this knowledge, students will be able to develop real-time applications using appropriate data structures. Finally, the course will enable students to identify the most suitable data structure to solve various computing problems.
Courses for this semester
Introduction to Information Security is a graduate-level introductory course in information security. It teaches the basic concepts and principles of information security and the fundamental approaches to securing computers and networks. Its main topics include security basics; security management and risk assessment; software security; operating systems security; database security; cryptography algorithms and protocols; network authentication and secure network applications; malicious malware; network threats and defenses; web security; mobile security; legal and ethical issues; and privacy.
This course will help students gain experience in various processes used in the Software industry for the development of a software product. They also learn about testing and maintenance of software products.
This course provides students to understand of the fundamental concepts of computer networking and communications make use of IEEE standards in the construction of LAN, build the skills of subnetting and super netting, explain the concepts of protocols of Transport Layer, QoS, and Congestion control mechanisms, and demonstrate different protocols of the Application Layer.
This subject aims to introduce students to the Java programming language. Upon successful completion of this subject, students should be able to create Java programs that leverage the object-oriented features of the Java language, such as encapsulation, inheritance, and polymorphism; use data types, arrays, and other data collections; implement error-handling techniques using exception handling, create and event-driven GUI using Swing components.
This course is an introduction to routing technology, routing theory, and router configuration including RIP and IGRP routing protocols, distance vector and link state routing theory, routing loop issues, routing concepts, TCP/IP basics, IP addressing, router IOS, access lists, and basic router configuration. Students will get hands-on experience configuring Cisco routers. This course also provides additional information on routing theory and protocols beyond that of the basic Cisco Networking Academy semester two course, leading to a more detailed understanding of routing.
This course covers software design, implementation, and testing using Java. It introduces object-oriented design techniques and problem-solving. The course emphasizes the development of secure, well-designed software projects that solve practical, real-world problems.
The objective of the course is to present an introduction to database management systems, with an emphasis on how to organize, maintain and retrieve - efficiently, and effectively - information from a DBMS.
The major objective of this lab is to provide a strong formal foundation in database concepts, technology, and to groom the students into well-informed database application developers. It also presents SQL and procedural interfaces to SQL comprehensively .The course gives an introduction to systematic database design approaches covering conceptual design, logical design, and an overview of physical design.
Courses for this semester
The Cyber Security and Blockchain program aims to train efficient Computer Science graduates with a comprehensive knowledge of cyber-crime, network security, threat intelligence, and Cryptography. The focus of the program is on data protection and smart contract enforcement mechanisms. This field is quickly transforming from a niche to a necessity in any organization. Students in the B.Tech program can begin their careers in this fast-paced industry.
This course introduces the core concepts of cloud computing. It helps to gain the foundational knowledge required for understanding cloud computing from a business perspective and becoming a cloud practitioner. The students can understand the definition and essential characteristics of cloud computing, its history, the business case for cloud computing, and emerging technology use cases enabled by the cloud. It introduces some of the prominent service providers (e.g. AWS, Google, IBM, Microsoft, etc.) and the services they offer, and look at some case studies of cloud computing across industry verticals.
This course continues NTNW 2351(CIS 2303, LAN Hardware and Software I). It covers all application software selection and installation details, hardware and software upgrades, and planning and testing for hardware and software upgrades. LAN utility software, and network interconnections. At least one leading LAN system will be used as a class and laboratory example.
Encryption algorithms all do the same job but can do it in very different ways. However, some features can be found across multiple families of cryptosystems. This course discusses some of the mathematical operations and structural design elements that can be found in many different cryptographic algorithms.
This course covers all the fundamental knowledge required to operate Datacenter Networks which consist of Cisco devices, Standard, and Cisco preparatory Data center technologies. Cisco Datacenter Networking Fundamentals Course Covers Networking, Network Virtualization, Switch Virtualization, and Machine Virtualization technologies and protocols. This course not only helps students to be prepared for the Cisco Data center exams but also provides a very broad level of knowledge on Cisco Data center Fundamentals technologies.
With this course, we begin networking. There are so many functions that need to be performed to be able to interwork different systems, a structure is required to be able to categorize and separate functions so that it is possible to discuss separate issues separately and not mix things up. The most commonly used structure is the ISO OSI 7-layer Reference Model. We’ll begin our discussion with some definitions, then an overview of the OSI model, introducing layers, layered architectures, and protocol stacks. In subsequent lessons, we’ll go through the layers individually and give examples of protocols like IP, TCP, LANs, and DSL to see where they fit into the stack. We’ll finish off understanding how a protocol stack works in operation, and conclude the course with a review of different active standards organizations.
Cybercrime poses serious economic and security threats to individuals, businesses, and governments. Cyberattacks have continued to increase in quantity as well as sophistication. In this course, the student will develop a solid understanding of the most common types of attacks used in cybercrime and cyberwarfare. Each session will begin with a lecture covering the basics of an area of technology and how that technology has been misused in the past. The student will then have the opportunity to participate in a hands-on lab, where with the guidance of the instructor and assistants, also learn and practice various techniques and tools to practice hacking into insecure systems. By learning about some of the most popular hacking techniques, you will develop an understanding of how to prevent them.
In this course, the new lab will give students a comprehensive way to build and manage a Windows Server 2022 server environment and explore how these core technologies can help organizations be more efficient, agile, and cost-effective.
Courses for this semester
This course is designed for the student who wants to go into the field of Computer Forensics or Digital Forensics. Computer Forensic is a comprehensive program focusing on the latest ways for data acquisition techniques and data retrieval techniques in a forensically sound manner so that the evidence can be presented in court. Real-time demonstration of the latest forensic techniques, methodologies, tools, tricks, and integrity measures.
Virtualization translates to creating a virtual counterpart of an existing system such as a desktop, server, network resource, or operating system. Holistically speaking, it is a technique that allows multiple users or organizations to make use of a single resource thread or an application among themselves. The course helps to understand the technologies and applications of cloud computing and its virtualization foundation is used in servers, along with data security tools.
This course is designed to introduce students, working professionals, and the community to the exciting field of cybersecurity. Throughout the course, participants will engage in community discourse and online interaction. Participants will gain knowledge and understanding of cybersecurity and its domains. They will engage with expertly produced videos, gain insight from industry experts, participate in knowledge assessments, practice assessing their environmental awareness, and gain access to materials that address governance and risk management, compliance, business continuity and disaster recovery, cryptography, software development security, access control, network security, security architecture, security operations, and physical and environmental security. Learning will be assessed using strategies aligned with knowledge and understanding. You do not need prior experience in IT security to do well in this course.
The course Linux Administration helps the students to work with Linux systems. Linux is an operating system, which is available as free and open-source software. Linux system administration is one of the most in-demand skills in the IT industry. This course will help the students to understand the fundamentals of Linux, Linux commands, and the manipulation of files and also how to install Linux, network and process management, and the Unix file system.
IT Infrastructure Library - (ITIL) is the most widely adopted framework for IT Service Management in the world. It is a practical approach to identifying, planning, delivering, and supporting IT services to the business. It describes how IT resources should be organized to deliver business value, documenting the processes, functions, and roles of IT Service Management (ITSM). ITIL principles are used by several organizations in both the public and private sectors such as NASA, IBM, HP, British Telecom, HSBC bank, and L'Oreal.
Cloud Computing (CC) represents a recent major strategic shift in computing and Information Technology. This course explores the fundamental principles, foundational technologies, architecture, design, and business values of CC. Understanding will be reinforced through multiple angles including analysis of real-world case studies, hands-on projects, and in-depth study of research developments.
This course will help correctly define and cite appropriate instances for the application of computer forensics and Correctly collect and analyze computer forensic evidence. Also to identify the essential and up-to-date concepts, algorithms, protocols, tools, and methodology of Computer Forensic.
This course will give a strong foundation in fundamental utilities needed for daily work on modern operating systems. It will develop the ability to write effective shell scripts that enhance the usefulness of computers for programmers and application developers. In addition, the course will enhance a good understanding of various OS-related concepts from a programmer's perspective, such as files, directories, kernels, inodes, APIs, system calls, processes, signals, and more. Students will have the ability to develop applications that require communication between multiple processes to complete tasks, using different IPC ways such as Message Queues, Semaphores, and Shared Memories. They will also develop the skills to write programs that employ advanced concepts like multithreading and useful programs for networking purposes.
Courses for this semester
This course aims to approach network security for Mobile, Wireless, and VoIP networks. It talks about the basics of mobile and wireless communication giving the students complete knowledge about the working, protocols, and methods employed to achieve end-to-end network security. Wireless networks are prone to severe security threats. This course covers security methods used in Mobile, Wireless, and VoIP networks, the methods and techniques used in mobile forensics, and their importance.
Microsoft Azure is a collection of online services that organizations can use to build, host, and deliver applications. The students don’t need to have their own data center because Azure runs in Microsoft’s data centers around the world. Not only does this approach save them the trouble of having to build and maintain their own on-premises IT infrastructure, but it can also save their money, because the students only have to pay for what they use, and they can scale their Azure resources up and down as needed. In this course, the students will not only get an overview of the Azure services available in various categories, such as compute, storage, and networking, but they will also follow hands-on examples showing how to create virtual machines and web apps using Azure Portal and Azure command-line interface.

CST- Common scholarship test is a national and international level online MCQ based examination funded for intellectual empowerment by Assam down town University.
CST- Maximum enrolment each year is 120 seats and any 10+2 students can apply. Adtu is northeast India’s first placement driven university to provide 100% scholarship benefits worth 10 cr.
CST aims to inspire brilliant and competent students to pursue further education. Accredited with a prestigious grade by NAAC, UGC and AICTE.
Explore more scholarships that can help you reach out your goal with financial aid.
This scholarship is valid on the basis of the board/university examination
| 95% & above | 100% Scholarship on all semester |
| 90%-94.9% | 50% Scholarship on all semester |
| 80%-89.9% | 25% Scholarship on all semester |
This scholarship is valid on the basis of the board/university exam
| National & International Level | 100% Scholarship on all semester |
| State Level | 50% Scholarship on all semester |
| District Level | 25% Scholarship on all semester |
This scholarship is valid on the basis of the board/university exam
| National & International Level | 100% Scholarship on all semester |
| State Level | 50% Scholarship on all semester |
| District Level & NCC Certificate Holder | 25% Scholarship on all semester |
Discover a multitude of world-class amenities and cutting-edge resources at Assam down town University, enhancing your academic journey to new heights.
The Start-Up & Incubation Centre at Assam down town University provides a supportive environment for young entrepreneurs to develop and grow their business ideas. The center provides mentorship, funding, and networking opportunities to help innovative ideas become successful businesses.
SFURTI scheme to support rural entrepreneurs and innovators, an initiative by the Ministry of MSME
TIDE 2.0 scheme for ICT-based startups which provides a grant of Rs. 4L and Rs. 7L under EiR and Grant categories respectively, an initiative by the Ministry of MeitY.
dtVL Ideation, an incubation program for early-stage entrepreneurs with a market-ready solution/product, offering interest-free loans up to Rs. 2 lakhs.
Sprout UP, an incubation program for students, faculties, and researchers with innovative business ideas, prototypes, or technology solutions.


















































"I am a BBA student of 3rd semester. I hail from Bhutan. I vow that I am having a great experience i...
"AdtU is amazing. I am a BBA student of 2019-22 batch and I am just grateful for the amount of oppor...
Let us be grateful to the people and place who makes us happy. They are the charming gardeners whom ...
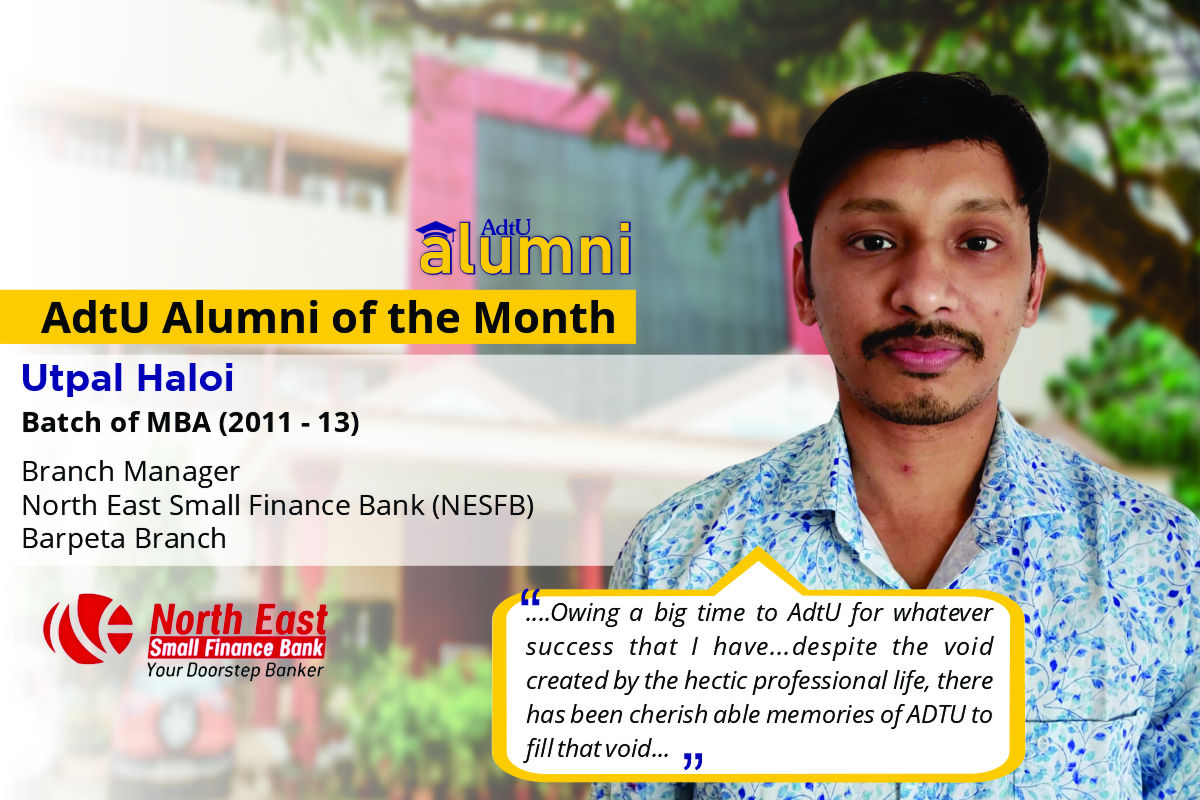
Currently I am pursuing MBA in Assam Down Town University. MBA is the professional course through wh...
AdtU is a university that focuses on giving knowledge, education and simultaneously making the stude...
The Assam downtown University has been a great learning experience. The university has provided me w...
My experience with AdtU has been splendid one indeed. Little needs to said about its scenic infrastr...
As a student I am very glad that I have got an opportunity to study here in Assam downtown universi...
My name is Sakhyajit Roy. I?m from Tripura. I joined the university on Auguest, 2017 as a student of...
I share immense pleasure to share my post graduate program experience in Assam down town University....
AdtU is a platform where I got golden opportunities to feed my zeal for knowledge through the dynami...
I am fortunate to get an opportunity to study here in Assam Downtown University. The best thing abou...
Our university is one of the best place for developing ourselves in the field of research and acedem...
ADTU is a university that is very good interms of infrastructure, academics and placements. Our tea...
It is one of best private colleges in North East India, it also provides a good environment for ed...
ADTU is a good University which provides the students with best quality lectures and ensures comfort...
The environment of Assam downtown university is very pleasant.The department of BMLT is very good a...
The university has all the necessary facilities and amenities for students . The classrooms and the ...
Assam downtown University is well recognised all over india. In the ongoing pandemic situation it ha...